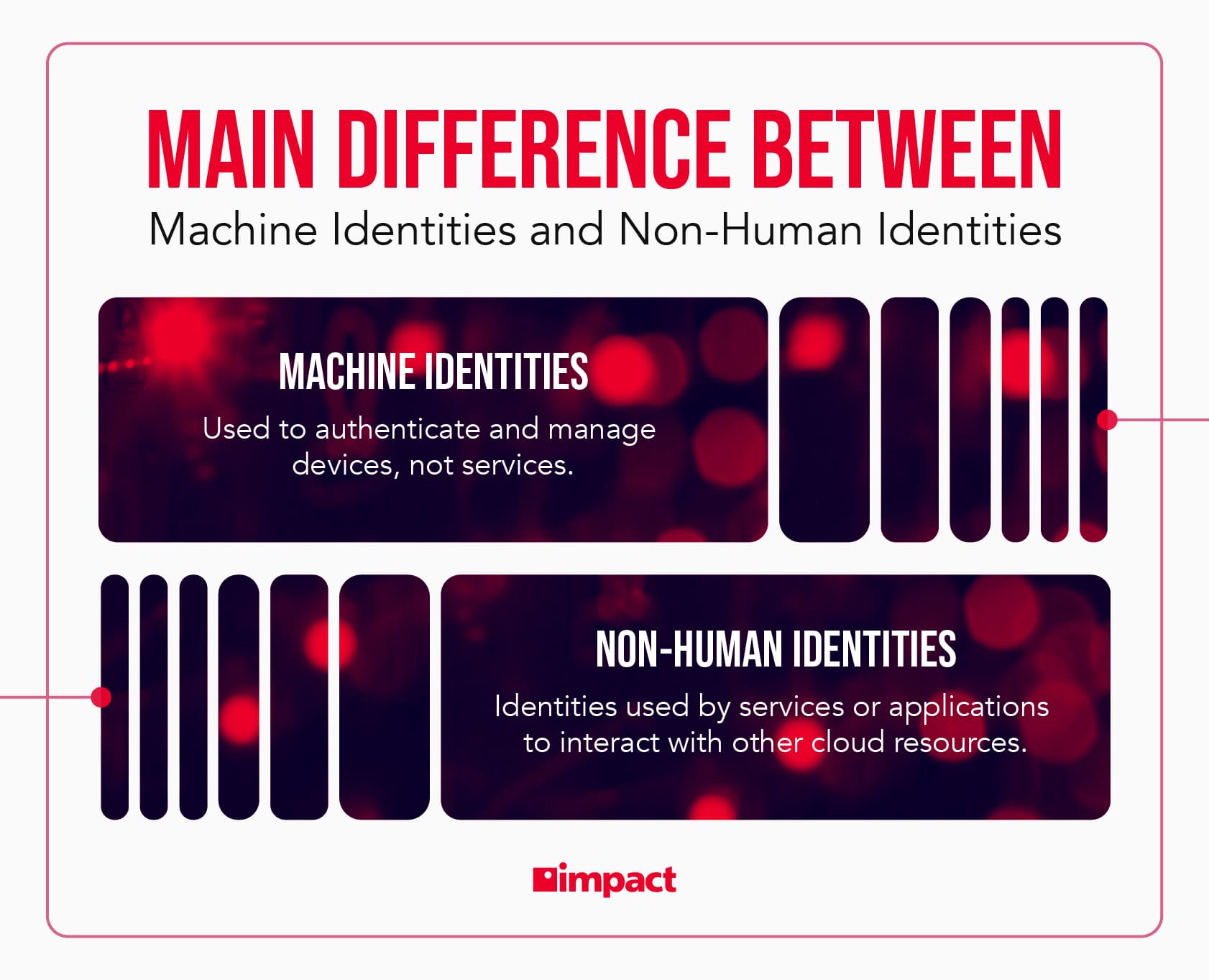
The non-human identity has quietly become foundational to daily operations. These digital identities power everything from service integrations and scheduled tasks to cloud workloads and API traffic, often without drawing much attention.
But, as their numbers grow, so do the risks and opportunities tied to how they’re used.
This guide breaks down what non-human identities are, why they’ve become so widespread, and how organizations can use them strategically. Whether you're overseeing security, infrastructure, or operational budgets, understanding the role these identities play is key to scaling with confidence and control.
For more information on keeping your business, your data, and your employees safe, watch Impact’s webinar, The Safety Debate: Cybersecurity Expert vs. Business Leader.
For example, imagine a virtual assistant built to automatically update customers after they place an order. In this instance, we can name our bot Nia. Nia can:
- Automatically confirm customer orders and send shipping updates.
- Notify customers of delays as they occur.
- Respond to customer inquiries on order status updates.
As you can see, these identities function much like user accounts, but instead of belonging to employees, they are assigned to API keys, service accounts, containers, and bots. They support automation and allow modern infrastructure to communicate and operate efficiently.
In most organizations, non-human identities now outnumber human users by the thousands. Unlike employee accounts, they often bypass traditional governance and accumulate excessive permissions over time. This creates unmanaged access points that increase risk across the business.
By understanding and controlling non-human identities, leaders can strengthen security, support compliance, and reduce exposure without slowing innovation.
Why Non-Human Identities Are Rising in Popularity
The rise of cloud-native infrastructure, automation, and API-driven services has fueled a sharp increase in non-human identities. As organizations adopt containerized workloads, serverless functions, and continuous integration/continuous delivery (CI/CD) pipelines, each tool and process needs its own identity to interact securely with other systems.
These identities keep operations moving at machine speed, enabling fast deployments and seamless integrations across environments.
Unlike human users, non-human identities scale automatically as new services spin up. A single application might generate dozens—or hundreds—of unique identities during its lifecycle.
This shift reflects a broader trend: businesses are relying less on manual intervention and more on interconnected systems that run continuously, communicate independently, and require precise access permissions to avoid disruption or downtime.
The Business Case for Non-Human Identities
Non-human identities unlock operational efficiency, scalability, and speed that manual workflows simply can't match. They allow businesses to automate high-volume tasks, coordinate services across hybrid and multi-cloud environments, and maintain uptime without constant human oversight.
This translates directly into faster delivery cycles, reduced overhead, and improved service consistency.
More importantly, these identities support secure, repeatable access across complex systems. When managed properly, they help enforce the principle of least privilege at scale, reduce credential sprawl, and strengthen auditability.
For organizations investing in digital transformation, non-human identities aren't just a technical requirement. They're critical in enabling business agility and control.
Ignoring non-human identities puts efficiency and security at odds. When handled strategically, these identities create a path to both, helping teams move faster while locking down critical access with precision. That balance gives businesses a competitive edge in fast-moving markets.
3 Benefits of Using Non-Human Identities
When properly managed, non-human identities deliver measurable advantages across performance, security, and operational efficiency. These identities streamline tasks that human users can’t perform at scale and ensure that systems stay connected, responsive, and secure around the clock.
Below are three core benefits that matter most to business and technology leaders alike:
1. Consistency and Reliability at Scale
Non-human identities allow systems to operate with precision and consistency, even in high-volume or distributed environments. Tasks like backup routines, data synchronization, and API calls run without interruption, reducing the risk of human error and boosting reliability across services.
2. Faster, Safer Automation
By securely authenticating processes and services, non-human identities remove the need for manual intervention. This accelerates deployment timelines and eliminates delays tied to human availability, while still enforcing access controls that align with security policies.
3. Granular Access Control
Unlike shared credentials or legacy service accounts, non-human identities can be tightly scoped. Assigning clear boundaries for what each identity can access improves compliance, strengthens audit trails, and supports a least-privilege model that minimizes exposure.
Security Challenges with Non-Human Identities
Non-human identities often lack visibility and oversight, making them a blind spot in many security programs. Unlike employee accounts, they don’t log in through a dashboard or trigger access reviews, which makes it easy for them to accumulate excessive privileges or go completely unmonitored.
As environments scale, so does the complexity of tracking what each identity can access—and why.
Hardcoded credentials, long-lived tokens, and unmanaged service accounts are common weak points. Attackers know this, and they actively exploit these gaps to move laterally, exfiltrate data, or maintain persistent access.
Without centralized governance, it becomes difficult to enforce least privilege, rotate secrets, or decommission identities no longer in use. These gaps don’t just increase exposure; they create silent opportunities for cyber criminals.
The Role of IAM in Using Non-Human Identities
Identity and access management (IAM) provides the structure and controls needed to manage non-human identities at scale.
It defines who or what can access specific systems, under what conditions, and for how long. IAM enforces authentication, authorization, and policy enforcement across automated workflows and machine-to-machine interactions.
A strong IAM strategy assigns unique identities to services, rotates credentials automatically, and limits access to only what’s necessary. It also centralizes visibility, allowing teams to audit activity and catch anomalies early.
In fast-moving environments, IAM lays the foundation for deploying non-human identities securely and strategically, with full control and accountability.
Wrapping Up on Non-Human Identities
Non-human identities have become essential infrastructure in modern business operations. They enable automation, improve consistency, and support secure, scalable access across increasingly complex environments. But without proper management, they also introduce real risk.
By taking a structured approach, grounded in IAM practices and aligned with business goals, organizations can unlock the full value of non-human identities while keeping systems protected and accountable.
As digital ecosystems continue to grow, getting this right now becomes a strategic advantage instead of a significant security weakness.
Watch Impact’s webinar, The Safety Debate: Cybersecurity Expert vs. Business Leader, for more information on the importance of investing in cybersecurity for your business.