In 2014, the US government created and published the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), which sets out a number of recommended standards that organizations in the public and private sectors can follow to improve their cybersecurity.
The US Department of Commerce, which NIST falls under, released an updated draft of the NIST Cybersecurity Framework to offer guidance to government agencies, industry, and other organizations on how to make these guidelines more effective and enforceable. The final version of the NIST 2.0 framework was published on February 26th, 2024.
Better protect your company by learning what causes breaches in cybersecurity, how businesses are affected by them, and how they can be stopped, by watching Impact’s webinar, Dissecting Cybersecurity Breaches: How they Happen & How to Stop Them.
What Is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is used to help organizations reduce cybersecurity risk. It’s important to note that all businesses have different risks, and, therefore, organizations’ implementations of the framework should vary.
The framework is designed to help companies understand and evaluate cybersecurity threats, prioritize opportunities to improve risk management, and establish a universal language for communicating about cybersecurity concerns, needs, capabilities, and expectations.
The NIST framework was ostensibly established to provide guidance for companies that operate in supply chains for the federal government like prime contractors and subcontractors. The standards, however, are applicable to all businesses. For those organizations that lack a cybersecurity strategy and need a jumping-off point, the framework is a great way of getting one.
For businesses with existing cybersecurity programs, the NIST Cybersecurity Framework can be leveraged to strengthen cybersecurity risk management. Many managed security service providers (MSSPs) will use the framework to determine what a business’ position is and what they need to do with their strategy going forward.
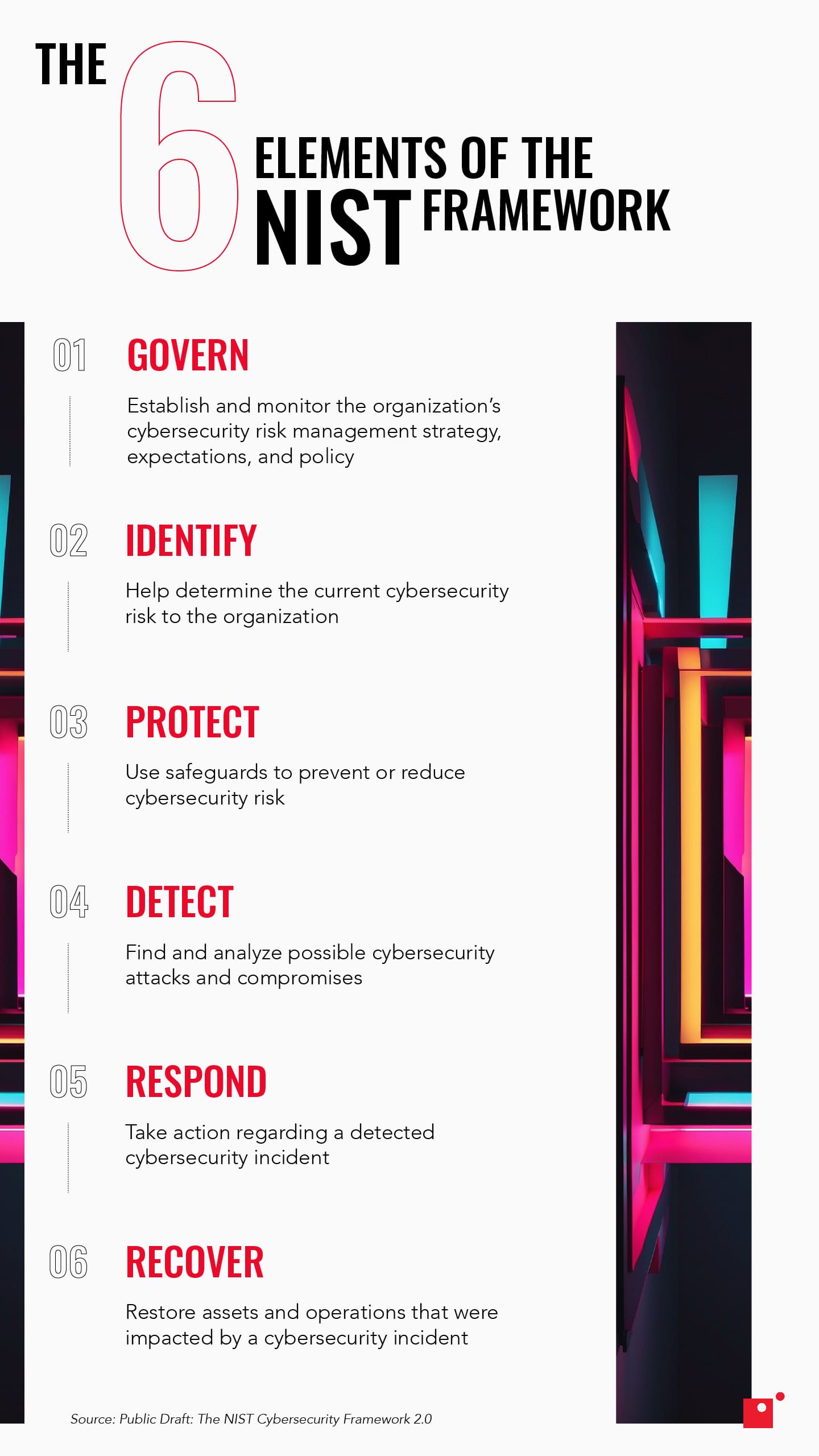
There are six key functions of the NIST framework:
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
Digging Into the 6 Elements of the NIST Framework
1. Govern
With the governance element, a company can decide how it will achieve and enforce the other five.
This stage is the newest to be added and is crucial for pragmatically integrating cybersecurity into an organization’s broader risk management strategy.
The tasks associated with governance include the development of cybersecurity strategy and cybersecurity supply chain risk management, as well as the supervision of cybersecurity strategy.
2. Identify
In the identification phase of the NIST framework, organizations need to conduct an audit and determine which of their systems are truly vital for their operations.
Once this audit is completed and you have an idea of your most important core systems, it can inform your cybersecurity strategy to prioritize protecting these processes.
3. Protect
After identifying your core systems and writing out a strategy that prioritizes their defenses, you need to actually implement those cybersecurity safeguards and practices.
By including awareness and training, data security, identity management, authentication, access control, platform security, and the resilience of technology infrastructure, organizations can prevent or lower the chances of harmful cybersecurity incidents.
4. Detect
A powerful cybersecurity strategy includes constant monitoring. Since cyberattacks are typically silent, you need systems and cybersecurity professionals in place who know where to look for breaches and what for the signs of those breaches are.
By detecting cyber threats immediately, you have a much better chance of mitigating potential damage.
5. Respond
If a cyber threat is detected, it’s up to the cybersecurity team to respond. This involves communication, damage mitigation, isolation, and event analysis—the why and how behind the attack.
The response element covers analysis, mitigation, communication, reporting, and incident management.
6. Recover
The last component of the NIST framework is recovery, which involves a well-established business continuity strategy that should be written out as part of the larger, comprehensive cybersecurity strategy.
Disaster recovery and business continuity plans will prepare you for the worst, so having a thought-out action plan to follow in the case of a successful cyberattack against your business is vital.
The 4 Cybersecurity Framework (CSF) Tiers
While the four different NIST cybersecurity framework tiers indicate how strong an organization’s cybersecurity strategy is, they are not a rigid framework. Rather, the tiers act as more of a guide for finding ways to improve the security posture as a whole.
Below, we explore each of the CSF tiers in a little more depth.
1. Partial
Organizations at tier 1 are just beginning their cybersecurity journey. Their approach is largely reactive, driven by immediate threats rather than strategic planning. There’s little to no formal risk management process, and cybersecurity responsibilities may fall to whoever happens to be available.
Key characteristics:
- No standardized policies or procedures
- Limited awareness of cybersecurity risks across the organization
- Minimal coordination between departments or external partners
This tier often reflects startups or small businesses with constrained resources, or larger organizations that haven’t prioritized cybersecurity. While not ideal, it’s a starting point—and recognizing the need for improvement is the first step toward building a more resilient posture.
2. Risk-Informed
At tier 2, organizations begin to understand the importance of cybersecurity and take steps to address it. Risk management practices are acknowledged and may be documented, but they’re not consistently applied across the enterprise. Cybersecurity decisions are informed by risk assessments, though these may be limited in scope or frequency.
What’s improving:
- Some formal policies exist, though enforcement may be uneven
- Business units start to factor cybersecurity into decision-making
- External collaboration begins, often in response to specific threats
This tier is common among organizations transitioning from ad hoc security to more structured approaches. The challenge here is consistency—without it, gaps remain that can be exploited.
3. Repeatable
Tier 3 marks a significant shift. Cybersecurity is no longer a reactive function—it’s embedded into the organization’s operations. Policies and procedures are well-defined, regularly updated, and consistently followed. Risk management is integrated across departments, and there’s a clear understanding of roles and responsibilities.
Defining features:
- Organization-wide cybersecurity governance
- Regular training and awareness programs
- Proactive engagement with external partners and industry groups
This tier enables scalability. As the organization grows, its cybersecurity practices grow with it. It’s a strong foundation for resilience, especially in industries with regulatory requirements or high-value data.
4. Adaptive
Tier 4 organizations treat cybersecurity as a dynamic, strategic asset. They continuously refine their practices based on real-time threat intelligence, lessons learned, and predictive analytics. Cybersecurity is deeply embedded in the culture—from the boardroom to the front lines.
What sets this tier apart:
- Continuous improvement driven by data and feedback
- Advanced threat detection and response capabilities
- Active participation in cross-sector information sharing
These organizations don’t just respond to threats—they anticipate them. Cybersecurity is aligned with business goals, enabling innovation while managing risk. Tier 4 is rare, but it’s where the most forward-thinking companies aim to be.
Why Is the NIST Cybersecurity Framework Necessary?
Cyberattacks have been on the rise at an alarming rate in recent years—with an estimated 560,000 new pieces of malware detected every day, according to Forbes—making it more important than ever for organizations and businesses to start thinking about their current cybersecurity practices.
The NIST framework components aim to provide businesses with a cybersecurity guide that will help them mitigate some of these rising cyber risks.
Data breaches for enterprise organizations can be devastating. One of the worst expenses an organization in today’s digital-first economy can incur is the cost of downtime. Downtime is exactly what it sounds like; it’s the amount of time that an organization isn’t operational due to its core systems going offline.
Downtime is a double-edged sword, too. Not only does downtime hinder a business’s ability to make active sales and result in significant losses, but it also has the potential to hurt its reputation with current consumers.
Turning the Page on the NIST Cybersecurity Framework
The NIST CSF provides a guide for organizations to enhance their cybersecurity. With six key functions—govern, identify, protect, detect, respond, and recover—the framework can help organizations protect crucial information.
In the face of increasing cyber threats and challenges, the NIST framework remains an indispensable tool for companies to navigate and strengthen cybersecurity systems.
Secure your company by tuning into Impact’s webinar, Dissecting Cybersecurity Breaches: How they Happen & How to Stop Them, to gain insights into the origins of cybersecurity breaches, their impacts on businesses, and effective prevention strategies.