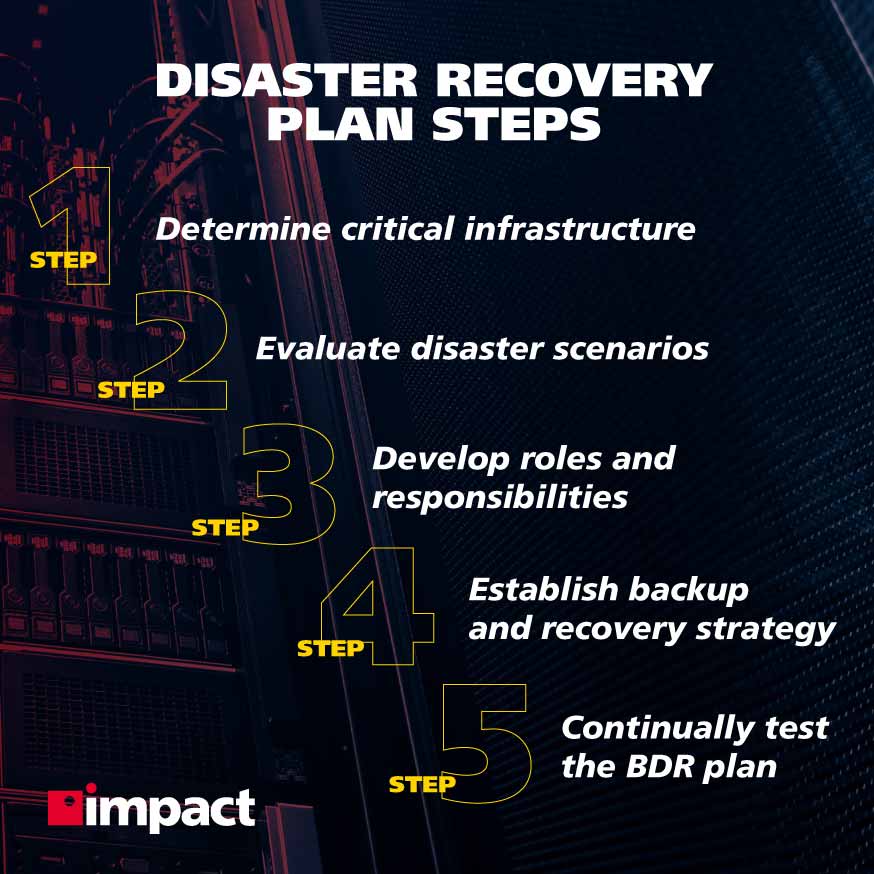
Take a look at these disaster recovery steps to get a clear understanding of what a business should have in place to counter a breach should the worst happen.
Nobody wants it, everybody hopes it won’t happen to them, and yet inevitably it will happen to someone. What are we referring to? Data breaches.
In 2020, a total 155.8 million individuals in the United States were affected by data exposures—the accidental revelation of sensitive information as a result of inadequate information security.
With concerns about cybersecurity growing each year and an increasing amount of SMBs falling victim to attack, it’s never been more important for organizations to have disaster recovery plan steps in place so that they can respond effectively to cybercrime.
Cyber criminals have shifted their focus in recent years, targeting more small businesses, resulting in a 424% increase in new breaches between 2017 and 2019. This trend has continued to today.
Today, we’re going to be walking through the steps a managed service security provider will take to ensure a business is fully prepared in the event that a breach occurs.
Without further ado, let’s dive in.
Step 1: Determine Critical Infrastructure
One of the most crucial steps in a disaster recovery plan is undoubtedly understanding your core critical infrastructure which is necessary for business operations to continue.
The primary function of a disaster recovery plan should be to restore critical business functions in order to avoid downtime.
Downtime—the loss of critical business functions—is extremely expensive. 80% of SMBs that experience downtime lose at least $20,000 per hour.
During this step, the business should be assessing exactly what these functions are—they will almost certainly concern the data and software needed to ensure product or service delivery.
The question organizations should be asking themselves is whether the loss of certain functions will cost them money, and if so, how much, and for what length of time would these losses be incurred?
Furthermore, the impact on customers should also be considered—if they don’t have access to your services, how much will be lost by them taking their custom to another business?
These are the key questions that should be recognized in order to determine what the most critical functions of a business are.
Once that has been established, the disaster recovery plan’s primary objectives in terms of maintaining critical infrastructure operations can be confirmed.
Step 2: Evaluate Disaster Scenarios
Now that you know what you must keep running to keep your business ticking, it’s important to lay out your potential disaster scenarios—how they will affect different departments and what will your RPO and RTO be? (We’ll get into this very shortly).
Businesses should consider which disaster scenarios are most likely to affect them—whether it’s a cyberattack or a natural disaster—and the impact it will have on them as far as operations go.
In a given disaster scenario, what would be required of the organization to continue, be it physical or digital?
How long would it take to relocate in a natural disaster? What would happen if you were hit by a ransomware attack?
These scenarios will differ significantly in their effects depending on the department, and business leaders from each should assess likely scenarios that may affect their specific department.
Step 3: Develop Roles and Responsibilities
Now that the critical infrastructure has been highlighted and the most likely disaster scenarios established, it’s time to create a communication plan that very clearly outlines the responsibilities of key stakeholders in the event of a disaster.
This can be as simple as reporting an incident to a superior or as complex as engaging with internal IT or a managed security service provider—whatever the responsibilities of individual stakeholders, it’s critical that a clear chain of communication is in place so that incident response teams can be involved in the disaster recovery process as quickly as possible.
This is also the time to develop an external communication strategy.
In the event of a breach, customers and clients should be informed of what is happening and the extent to which they are affected.
Social media managers and communications staff should be clear in their responsibilities as far as online communication is concerned, communicating what actions are being taken to ensure their information is being safeguarded.
Step 4: Establish a Backup and Recovery Strategy
Now the most important part: putting a plan in place to backup and recover data that is essential to the running of business operations—this should have been established during the assessment of critical infrastructure.
At this step in the disaster recovery plan, the organization will want to understand what their RPO and RTO are.
RPO: Recovery Point Objective
The RPO represents the tolerance a company has to data loss. In other words, how much data can be lost before the business begins to incur significant or irreparable damage?
The recovery point objective is measured as the time that is acceptable between the disaster and the time at which data is restored.
If it is determined that the RPO is two hours, that means the company can survive two hours of data loss before it’s considered unacceptable.
In this example, an RPO of two hours would mean that the organization requires a backup every two hours in order to ensure no more than that is lost in the event of a disaster.
RTO: Recovery Time Objective
The RTO is very similar to RPO, except as opposed to RPO—which determines the point in the past at which you will recover your data—RTO refers to the point in the future before which data must be recovered or else unsustainable damage will have been inflicted.
It’s best to think of RPO as the data recovery point in the past and the RTO as the time in the future at which critical business functions must be up and running again.
Ideally, the RTO and RPO would be fractions of a second, but backing up and recovering data in such a minute amount of time would be both unimaginably expensive and simply unfeasible—at least for now.
Because of this, businesses must establish their RPO and RTO in order to understand the absolute maximum period of time into the past and future that their business can withstand before irreversible damage is done.
Once both of these are established, the business can implement a backup plan that ensures their data will be restored by at least the desired RPO and RTO times.
Step 5: Continually Test the BDR Plan
The final disaster recovery plan step is to consistently test and re-test it to ensure the strategy is up-to-date and still relevant.
The reason for this is that IT environments change constantly—workforces grow and shrink, new software is installed, more data is stored; there are many variables that can change the outlook of a BDR strategy.
Therefore, it’s highly recommended that periodic reviews that test the plan are conducted.
During these reviews, several factors should be considered to ensure that IT infrastructure is being tested appropriately.
Namely, making sure the recovery time and point objectives are within the correct timeframes and ensuring there are no single points of failure and systems have sufficient redundancy.
Regular testing should be conducted indefinitely thereafter.
Using an MSP for Your Disaster Recovery Plan Steps
These disaster recovery plan steps presented are a basic overview of what’s involved when putting together a BDR strategy for an organization.
An increasing number of companies today opt for the services of a managed service provider to conduct an assessment of their IT infrastructure and offer a recommendation for the disaster recovery strategy necessary for the business.
MSSPs have the tools and expertise to conduct a comprehensive review of your systems, policies, and procedures and will be able to maintain a disaster recovery plan that will ensure the organization is prepared should disaster strike.
Impact’s cybersecurity program provides vital disaster recovery strategies that you can rely on to keep your organization up and running if disaster strikes by protecting critical infrastructure and safeguarding business-essential data. Learn more about our backup and disaster recovery services.