SentinelOne, a technology partner of Impact Networking, has offered several cybersecurity recommendations for businesses in light of recent tensions between the US and Iran.
While the threat of physical conflict has subsided, the threat of cyber conflict has, and will remain, a major concern for US organizations of all sizes.
As we push into the new decade, the number of attacks will grow.
In light of this recent tension, there’s a well-founded concern that Iran may seek to wreak havoc using cyberwarfare.
Cybersecurity is one of the most pressing issues for modern businesses, and heeding the cybersecurity recommendations of companies like SentinelOne to invest in protecting network infrastructure is vital.
Major Concern Among Decision Makers
Business leaders recognize this more than ever.
93% of SMB executives believe that as foreign adversaries attempt to breach national security of wage cyberattacks, small businesses like theirs will be used as entry points
For small and midsize businesses which only utilize basic security protection, the risks are greater than more typical targets like banks and government agencies.
Related Post: Advanced Cybersecurity: Why a Firewall Won't be Enough in 2020
They often lack substantial forms of protection, meaning SMBs are more vulnerable than larger organizations.
The stakes are higher too, with 93% of companies that don’t have a disaster recovery plan going out of business within just one year
The message to take from this is clear.
Cyberattacks will continue to be a threat and SMBs must be able to deal with them effectively.
SentinelOne Offers 6 Cybersecurity Recommendations
1. Disable unnecessary ports and protocols
“A review of your network security device logs should help you determine which ports and protocols are exposed but not needed.
“For those that are, monitor these for suspicious, ‘command & control’-like activity.”
2. Log and limit the use of PowerShell
“If a user or account does not need PowerShell, disable it via the Group Policy Editor.
“For those that do, enable code signing of PowerShell scripts, log all PowerShell commands and turn on ‘Script Block Logging’.”
3. Set policies to alert on new hosts joining the network
“To reduce the possibility of ‘rogue’ devices on your network, increase visibility and have key security personnel notified when new hosts attempt to join network.”
4. Backup now, and test your recovery process for business continuity
“It is easy to let backup policies slide, or fail to prove that you can restore in practice.
“Also, ensure you have redundant backups, ideally using a combination of hot, warm and cold sites.”
5. Step up monitoring of network and email traffic
“The most common vectors for intruders are unprotected devices on your network and targeted phishing emails.
“Follow best practices for restricting attachments via email and other mechanisms and review network signatures.
“Particular focus should be placed on external-facing hosts which are being targeted by password-spraying and brute-force login attempts.
“Externally-exposed systems, where multi-factor authentication can not be implemented, should be monitored carefully.
“Attempting to compromise VPN servers without 2FA (for example) is a well-established TTP for Iranian-based actors.”
6. Patch externally facing equipment
“Attackers actively scan for and will exploit vulnerabilities, particularly those that allow for remote code execution or denial of service attacks.
“Implement multi-factor authentication where necessary (ex: VPN servers).”
Future Mitigation for Small and Midsize Businesses
Most businesses are keen in one way or another to protect their business from cyberthreats.
But how?
Well, let’s have a look at the core components that you need to have covered in order to have a functioning security policy.
Perimeter safeguarding
Your network perimeter is the boundary between you (intranet) and the outside world (internet).
The Internet of Things era that we now find ourselves in has changed the game.
A plethora of new devices are connected to your network at any one point in time, meaning new challenges for security.
You should have a strong unified threat management solution for your perimeter defense.
This way, your network will be defended from any incoming threats, blocking malware and other malicious actors in real-time.
You should also implement a web application firewall (WAF) in order to inspect web traffic.
This gives you complete coverage, reviewing encrypted traffic and securing your site from threats like denial of service (DDoS) attacks.
Endpoint protection
As we just mentioned, the current prevalence of IoT devices means a lot more things to protect.
Laptops, phones, tablets, TVs, printers—all of them are likely connected to the network in any given office.
This creates a large number of new entry points for potential hackers.
In fact, the printer—often forgotten about by workers—is an incredibly vulnerable device and frequently attacked and used to infect networks.
This makes endpoint security a must.
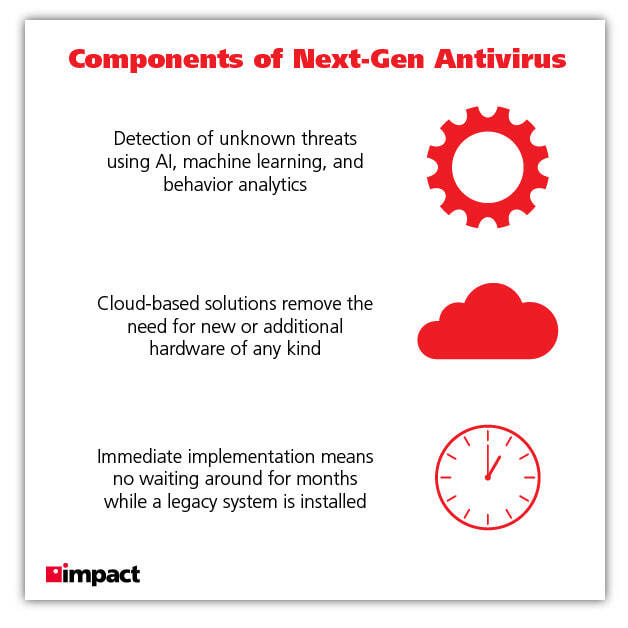
Businesses should do everything they can to ensure that all devices operating under network are adequately protected with a next-gen antivirus solution.
Related Post: What Is Next-Gen Antivirus?
Authentication
Advanced verification for users that are logging onto your network is a sure way to significantly improving your security.
It’s advisable that you have a credential management system which protects your passwords with solid methods of encryption.
Related Post: What Is Cyber Hygiene?
One of more rapidly pervasive methods of verification is the use of multi-factor authentication (MFA)
Though some find it annoying, the stats don’t lie.
Microsoft cloud services see 300 million fraudulent sign-in attempts every day.
They estimate that MFA blocks 99.9% of automated attacks.
In other words, it works and the difference MFA makes is substantial.
Backup & recovery
We noted before that an overwhelming number of small and midsize businesses that are victims of a cyberattack end up failing.
This is often because they have no structure in place to rapidly deal with an attack.
Disaster recovery is absolutely crucial and should never be neglected.
Related Post: Why a Disaster Recovery Plan is Vital for SMBs
With only 27% of businesses prepared for business continuity and one-third of businesses not testing their disaster recovery plans at all, there is a clear trend of SMBs not employing a strong strategy to counter cyberattacks
Downtime is expensive and should be mitigated at all costs.
You should have duplicate images of all aspects of your OS, including applications.
These images should be able to be delivered to you in a timely manner so an engineer can restore your systems and get you back up and running ASAP.
How MSSPs Are Helping SMBs
With more and more small and midsize businesses threatened by cyberattacks, there has been increasing demand for security partners.
Managed security service providers (MSSPs) are stepping in to fill the gaps, offering businesses an easy way to take care of protecting their data.
An MSSP will offer a wealth of experience, expertise, and top solutions for an affordable, fixed fee.
They will conduct an assessment, taking note of your current setup and provide you with a detailed breakdown of where your security is up to scratch and where it may need improving.
With a security partner, SMBs can rest easy knowing the experts are on the job.
The managed security services market was worth $27.7 billion last year; it’s expected to grow to $64.73 billion by 2025.
As cyberattacks continue in volume and scope, we anticipate the use of MSSP services to grow throughout 2020 and beyond.
Impact Networking’s managed security program provides vital cybersecurity protection for clients, keeping their minds at ease in the knowledge that their IT infrastructure is being monitored and maintained by our security experts.
We’ve vetted hundreds of vendors to ensure that our program utilizes best-in-class solutions for our clients. In today’s landscape, a comprehensive cybersecurity program has never been more important.
Learn more about Impact's managed cybersecurity services.