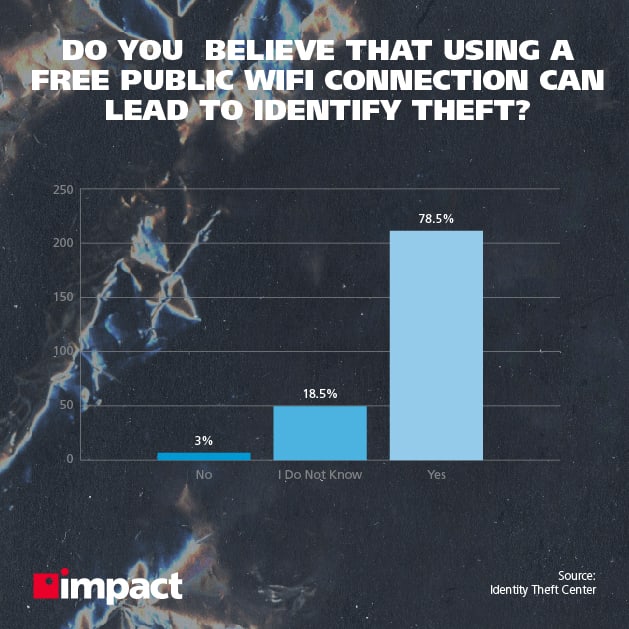
Nowadays, public WiFi security is paramount—because public WiFi risks are more severe than they’ve ever been.
We can almost always connect to the Internet for free, no matter where we may be, but the protections afforded can be limited at best.
However, WiFi hotspots, and let’s be completely honest here, are more comparable to public restrooms than they are a secured bank vault in terms of their security.
You can typically find them at convenient places, like a coffee shop or fast food restaurant, but in truth you’re better off avoiding them altogether.
The trouble is, we love using public WiFi.
After their own homes, the second-most common place for employees to conduct remote work is in coffee shops, with 37% of professionals indicating they use them.
In other words, free, public WiFi Internet access lacks security, to put it mildly. What’s more troubling is that a lot of people don’t really realize just how unsafe these networks actually are.
You simply connect, and the sensitive information you share on your device over the public network is vulnerable to hackers.
Therefore, if you have to use public WiFi for any reason, you might as well ensure that your data is protected and safe from theft.
Businesses should be more concerned than ever about risky public WiFi use, particularly considering the staggering number of them falling victim to attack—as many as 90% of organizations internationally experienced targeted phishing attacks in 2019.
With that in mind, here’s how to keep your online data safe while using a public WiFi connection.
Decide which Wi-Fi to connect to
The catch with free WiFi is that it’s a network someone maintains without getting anything in return.
In other words, they don’t earn money from it and no one does this out of the goodness of their hearts, so don’t expect any of the usual protections you might find at the office.
For example, you may think your local coffee shop’s WiFi is familiar and more or less safe to connect to, but that doesn’t mean they have any security measures up and running.
Nevertheless, it’s always a better idea to connect to a WiFi connection you know than some random hotspot you came across somewhere on the street. The fewer Wi-Fi hotspots you connect to, wherever you may be, the fewer the chances are that you’ll stumble upon a scam network that leaves you open to attack.
63% of company departments have at least one person who works remotely for a significant amount of time, but 57% of businesses have no formal work-from-home policies.
These are known as “rogue” hotspots, whereby an attacker will set up a scam hotspot that looks as legitimate as any—then once you’ve joined they can conduct a man-in-the-middle attack in an attempt to steal your data.
And before you’re thinking this will never happen to you; this has been happening for many years. See here just how easy it is for someone to create a legitimate-looking hotspot and how many members of the public unknowingly connect to it.
Don’t connect to a public hotspot unless you’re sure it is what it says it is.
Use a secured device
You may not be able to control the security of a public WiFi connection, but you can control the security measures on your device.
Security software of some sort is an obvious and relatively pain-free way of ensuring another layer of security.
Even the free versions of antivirus or anti-malware software can provide the most basic form of protection while browsing public WiFi networks.
Furthermore, using a device that has built-in security protocols for accessing public WiFi networks is also a good idea.
For instance, modern devices that are compatible with the latest WAP3 security protocol can ensure a secure connection to an unsecured WiFi public network and protect both your data and your device from any data thefts, scams, or other potential hacking attempts, including brute-force password attacks.
WAP3 supported devices started rolling out in 2018, and since a lot of people can’t wait to get the new smartphone on the market, the chances are that you may well already have a device that can give you some level of protection on public WiFi networks.
Remote work has seen growth of 91% during the last decade, a trend that is likely to continue once we return to normal, so for many having an idea of how to handle public WiFi use will be good practice.
Control your connection
The fact of the matter is that you can control how you access public WiFi networks.
If a public WiFi hotspot lacks the proper security measures that will ensure data protection and a theft-free environment, you can create your own environment with adequate protection.
The way to do this is to use a VPN (Virtual Private Network).
Unfortunately, a lot of people don’t know what a VPN is or how to use one.
A VPN creates a private network within a public network, such as a Wi-Fi hotspot.
Basically, you connect to a VPN server that masks your online activity and encrypts your data while it’s in transit—in other words, it’s inaccessible from the moment it leaves your device to the moment it reaches its destination.
It’s best to think of a VPN as a kind of tunnel between you and the person you’re sending data to.
Therefore, even if a public WiFi connection is unsafe, you can still browse the web without worry, as well as be sure that some prying eyes aren’t watching your every move.
Using a VPN is not intrusive, nor do you have to be tech-savvy to know how to use it. If you need to access the public WiFi network, you might as well control the way you do this.
For businesses, using a VPN can be a crucial tool for ensuring that employees are safely handling data outside the office.
Browse safely
While surfing the Internet on the public WiFi connection, you want to make sure that your activity can be as hidden as possible.
Before you begin, make sure you turn off any file-sharing options on your device.
The last thing you want is to freely share files and data with other people on the public network or receive files from strangers without previously authorizing it.
Moreover, try to only browse websites that have HTTPS (Hypertext Transfer Protocol Secure).
This protocol encrypts communication between your device and the website you’re currently visiting. That way, you can prevent anyone from listening in, as well as prevent man-in-the-middle attacks.
On most Internet browsers, such as Chrome or Firefox, the HTTPS websites are marked with a padlock before the URL. That way, you’ll know that the website you’re about to visit is properly secured.
If there’s no communication encryption, it means that anyone can see what you’re doing, and they can easily highjack the communication or redirect you somewhere where your data can easily be stolen.
It’s not difficult to browse safely if you make an effort to determine how to do so. After all, it’s your data on the line.
Unfortunately, there’s no 100% guarantee that you’ll be safe online or that your data will be protected from thieves.
By adequately protecting your device and your data when accessing public Wi-Fi connections, you can avoid potential breaches and ensure that no one will steal sensitive information you have on your device.
Cybersecurity is one of the most important considerations a business can make, particularly in light of this year’s crisis. Employees have been forced from their offices and are having to conduct work through unverified networks.
Many organizations have found themselves playing catchup, trying to implement makeshift cloud solutions to make up lost ground while their workforces transition to remote work for the immediate future.
To find out more about how your employees can work safely while out of the office, take a look at our Remote Work Cybersecurity Checklist.