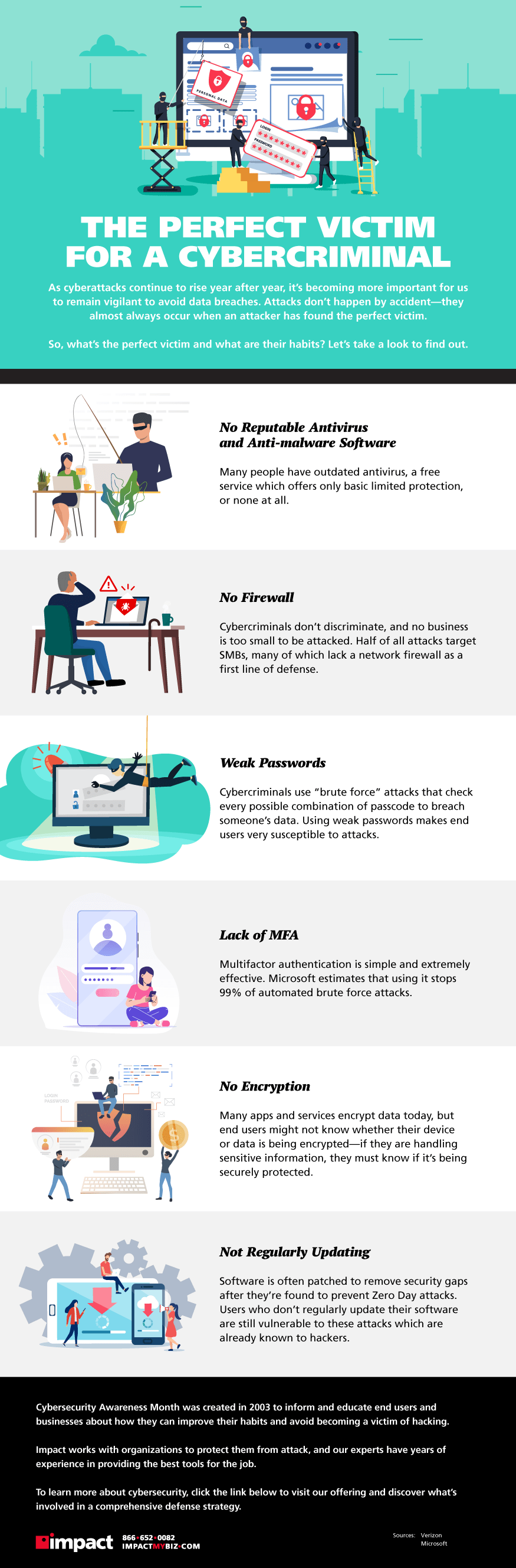
Cybercrime has been on the rise for a number of years, and a victim of cybercrime pays a hefty price. The events of 2020 have only sped along these attacks, which have increased in frequency dramatically this year.
Phishing emails have spiked by over 600% since the end of February 2020 as cybercriminals look to capitalize on the fear and uncertainty generated by the COVID-19 pandemic
Why have cyberattacks increased? Because people are more vulnerable than ever. Much of the reason of this is simply as a result of the dramatic shift that has taken place with regards to people’s work situations.
As businesses sent workers to do their jobs from home, many of them did so without ensuring they could work with the same protections that would be expected in the office.
In other words, there’s a lot of remote workers who are handling sensitive data as they normally would, only without the necessary security that should be afforded to such information.
Related Post: What Is Cyber Hygiene?
When you combine this with concerns that have long existed about the data security capabilities of organizations—SMBs in particular—and the concerns about employees being able to handle data effectively; you have a recipe for trouble.
96% of IT decision makers believe their organizations are susceptible to external cyberattacks, and 52% of businesses admit that employees are their biggest weakness in IT security
In this environment, hackers have spotted an opportunity, and sure enough, attacks have increased enormously this year as they look to take advantage.
The question is, what does a perfect victim look like to a hacker? If you recognize any of the following habits in the infographic as applicable to your own, then now’s the time to consider a change before it’s too late. Take a look!