What Does HIPAA Mean?
What is HIPAA exactly and what do you as a company need to do to stay on the right side of its associated regulations?
HIPAA stands for the Health Insurance Portability and Accountability Act, which was passed by Congress back in 1996.
HIPAA has since then been updated and built on, most notably with the 2009 HITECH act (Health Information Technology for Economic and Clinical Health) and the 2013 Omnibus Rule.
These together extended liability towards Business Associates and their subcontractors, as well as stricter protections on how PHI can be used as regards marketing and sales.
While HIPAA concerns a number of areas, including healthcare coverage for people losing or changing their job and tax-related provisions, our main focus will be on Title II of the law, which is about the exchange, security, and privacy of health data and what concerns the vast majority of businesses when it comes to compliance.
Let’s jump right in and go through all you need to know about HIPAA and what the keys to success are for HIPAA compliance.
What Is the Purpose of HIPAA?
As we just noted, HIPAA has several purposes outside of data protection—specifically related to health insurance law reform.
For most organizations researching HIPAA, however, their primary goal is to know what they need to do in order to stay compliant with its regulations and avoid the fines that come from non-compliance.
This area of HIPAA is all to do with data protection and privacy in relation to the disclosure and use of protected health information, or PHI.
HIPAA compliance and the security of PHI is critical to health organizations today.
Who Has to Abide By HIPAA?
Entities that have to abide by HIPAA compliance are known as covered entities.
Covered entities are people or companies that store, handle, and process PHI.
Covered entities, in addition to keeping in compliance with HIPAA, are also responsible for reporting violations relating to it.
The following individuals and organizations constitute covered entities:
Health Care Providers
- Doctors
- Clinics
- Psychologists
- Dentists
- Chiropractors
- Nursing homes
- Pharmacies
- Health Plans
Health Insurance Companies
- HMOs
- Company health plans
- Government-provided health care plans
Health Care Clearinghouses
- These are entities which facilitate the processing of nonstandard health information into standard data elements. These are effectively middlemen between healthcare providers and insurance payers.
Business Associates
- A “business associate” creates, receives, maintains, or transmits protected health information (PHI) on behalf of a covered entity or another business associate acting as a subcontractor.
Subcontractors
- A subcontractor that creates, maintains, or transmits protected health information (PHI) on behalf of a business associate has the same legal responsibilities as a business associate under HIPAA. In other words, privacy- and security-related legal responsibilities flow “downstream” to subcontractors performing work for a business associate.
Hybrid entities
- A hybrid entity performs both HIPAA-covered and non-covered functions as part of its business. A large corporation that has a self-insured health plan for its employees may elect to be treated as a hybrid entity. Other examples are a university with a medical center or a grocery store that has a pharmacy.
What Does PHI Encompass?
Personal health information (PHI) refers to any demographic information which can be used to identify a patient, client, or other entity.
There are 18 identifiers that make information relating to health considered PHI. These are:
- Names
- Dates, except year
- Geographic data
- FAX numbers
- Social Security numbers
- Email addresses
- Medical record numbers
- Account numbers
- Health plan beneficiary numbers
- Certificate/license numbers
- Vehicle identifiers and serial numbers, including license plate numbers
- Phone numbers
- Web URLs
- Device identifiers and serial numbers
- Internet protocol (IP) addresses
- Full-face photos and comparable images
- Biometric identifiers (fingerprints, for example)
- Any numbers or codes that uniquely identify someone
These are the types of data and information that must be protected in order to remain HIPAA compliant.
What Is Considered a HIPAA Violation?
A HIPAA violation occurs when compliance is not adhered to by an entity, and there are literally hundreds of ways individuals and organizations can fall foul of HIPAA compliance.
Common violations of HIPAA will typically involve one of the following:
- Unauthorized, impermissible, or unnecessary disclosure of PHI
- Unauthorized accessing of PHI
- Incorrect disposal of PHI
- Lack of conducted risk assessment by the entity
- Lack of risk management as regards PHI
- Failure to establish HIPAA compliance agreement with third parties when providing access to PHI
- Failure to provide security awareness of HIPAA training to employees
- PHI theft
- Sharing of PHI without prior permission
- Mishandling/unwarranted mailing of PHI
- Failure to notify individual of a security incident involving PHI within 60 days of breach discovery
- No documentation of compliance protocols, procedures, and management
What Happens If HIPAA Is Violated?
A HIPAA violation occurs when any aspect of the HIPAA standards and provisions are contravened. It's easy to find a full rundown of all HIPAA regulations published by the Department of Health and Human Services Office for Civil Rights.
If a violation is reported, the covered entity is subject to penalties, whether they be civil or criminal—penalties can vary significantly, depending on the violation.
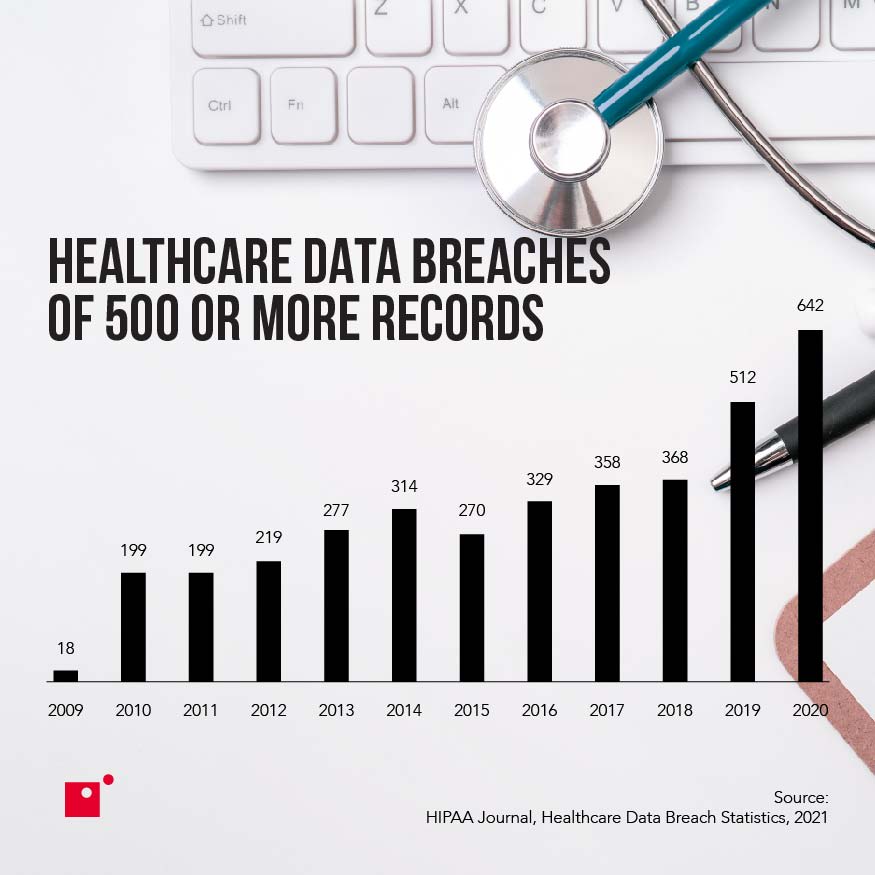
Typically, the US Department of Health and Human Services Office for Civil Rights (OCR) will investigate violations—and they will investigate all covered entities who report breaches of more than 500 records.
If the OCR determines that a particular case is criminal rather than civil, they will refer it to the Department of Justice.
In the majority of cases, individuals can expect to pay $100 per violation; repeat violations can cause fines of up to $25,000.
In cases where individuals have shown a willful neglect of HIPAA regulations and have made no attempt to correct their policies and procedures, a minimum penalty of $50,000 can be incurred, up to a maximum of $1.5 million.
In criminal cases, lesser sentences of a $50,000 and up to one year in prison are possible—with a $250,000 fine and up to 10 years in prison being the maximum.
For civil proceedings, violations are categorized into tiers, with 4 being the most severe.
They are as follows:
- Tier 1: A violation that the covered entity was unaware of and could not have avoided.
- Tier 2: A violation that the covered entity should have been aware of but could not avoid.
- Tier 3: A violation that occurred as a direct result of willful neglect, but where an attempt was made to rectify the violation.
- Tier 4: A violation constituting willful neglect where no attempt was made to correct the violation.
The penalties for HIPAA non-compliance for each tier are as follows:
- Tier 1: Minimum fine of $100 per violation up to $50,000
- Tier 2: Minimum fine of $1,000 per violation up to $50,000
- Tier 3: Minimum fine of $10,000 per violation up to $50,000
- Tier 4: Minimum fine of $50,000
Criminal proceedings are a little different, with three tiers and far more severe punishments than civil proceedings.
They are as follows:
- Tier 1: Reasonable cause or no knowledge of violation
- Tier 2: Obtaining PHI under false pretenses
- Tier 3: Obtaining PHI for personal gain or with malicious intent
Criminal penalties:
- Tier 1: Up to one (1) year in jail
- Tier 2: Up to five (5) years in jail
- Tier 3: Up to 10 years in jail
Can I Be HIPAA Certified?
At the time of writing this, there is no such thing as HIPAA compliance certification or verification.
Third parties may offer a form of “HIPAA certification”, but there is not an officially endorsed or mandated certification offered by HHS.
There is no standard or implementation specification that requires a covered entity to “certify” compliance. The evaluation standard § 164.308(a)(8) requires covered entities to perform a periodic technical and non-technical evaluation that establishes the extent to which an entity’s security policies and procedures meet the security requirements. – Office for Civil Rights (OCR)
So, while there is no HIPAA certification, many third party MSSPs can perform periodic assessments when necessary and ensure that you are in compliance with HIPAA.
What Is a HIPAA Officer?
A HIPAA officer is a compliance officer.
Whether they are in-house or hired as a third party, their primary job will be to ensure your HIPAA compliance by making sure your security and privacy protocols for PHI data are correctly enforced.
In instances where there is no such policy in place, the HIPAA officer will be responsible for developing and implementing a compliance plan for the individual or organization.
They will then be in charge of maintaining and monitoring the program, investigating and reporting where legally necessary and ensuring that patient or client data is being safeguarded as required by state and federal law.
What Is the Key to Success for HIPAA Compliance?
If you’ve been reading this piece (or skimming) and felt your pulse raising a little looking at the penalties for non-compliance, then don’t worry.
It doesn’t take a lot to ensure that you are compliant with HIPAA, but there are certainly some keys to success for HIPAA compliance that organizations would do well to follow.
First, you should seek out a managed security service provider who performs HIPAA assessments to come and audit your systems for HIPAA compliance.
Once they’ve performed the risk assessment, they will be able to recommend and carry out the implementations you need to make sure you are doing everything possible to maintain compliance.
What Is a HIPAA Risk Assessment?
Related Post: What Happens During a Cybersecurity Risk Audit?
A HIPAA compliance audit is the assessment performed by a compliance officer which will take a deep dive into your systems and security protocols.
First, they will need to collaborate with you in determining the scope of the audit—chiefly related to your obligations (in this case, HIPAA is the main priority, though you may need to be compliant with other regulations, too).
They will then draw up a schedule for the audit and proceed to the next stage; execution. This part involves vulnerability scanning, penetration testing, and a gap analysis.
In the case of a risk assessment for HIPAA compliance, a gap analysis will be essential, as this is where the HIPAA compliance officer will detail what needs to be done to bring you or your company into compliance.
Once the HIPAA compliance audit is concluded, the compliance officer will make their recommendations and you can get a clear understanding of what needs to be done.
You may also take this opportunity to delegate the implementation of these recommendations to the MSSP, in which case you can sign a long-term contract with them—allowing you to get on and run your business while the managed security service provider takes care of compliance.
If you’d like to learn more about HIPAA compliance and what a managed security service provider can do for you, take a look at our compliance services page.