When it comes to complex and technical topics like cybersecurity, the conversation, and more importantly, the strategy can quickly become daunting for non-technical professionals. Especially if they’re trying to tackle the implementation of security measures themselves.
With a little bit of guidance and direction, though, it can be a lot easier to identify your priorities and get the ball rolling with a set of agreed-upon cybersecurity initiatives that have proven to significantly enhance network security time and time again.
The Critical Security Controls (CSC) framework published by the Center for Internet Security (CIS) guides organizations through the pillars of cybersecurity, helping them focus their attention and resources on the security tactics that matter most.
If you need help implementing any of the Critical Security Controls listed in version 8, consider getting started with a strategic partnership that provides you with a team of experts ready to reinforce your entire cybersecurity posture.
The Critical Security Controls by the Center for Internet Security
The Center for Internet Security is a nonprofit organization dedicated to enhancing cybersecurity readiness and response for public and private sector entities worldwide. Founded in 2000, the CIS works collaboratively with experts in government, industry, and academia to develop best practices, benchmarks, and tools to help organizations improve their cybersecurity posture.
One of the key initiatives introduced by CIS is the Critical Security Controls framework. The CSCs represent a continually updated set of cybersecurity priorities, actions, and measures designed to mitigate the most common and damaging cyber threats that organizations face today.
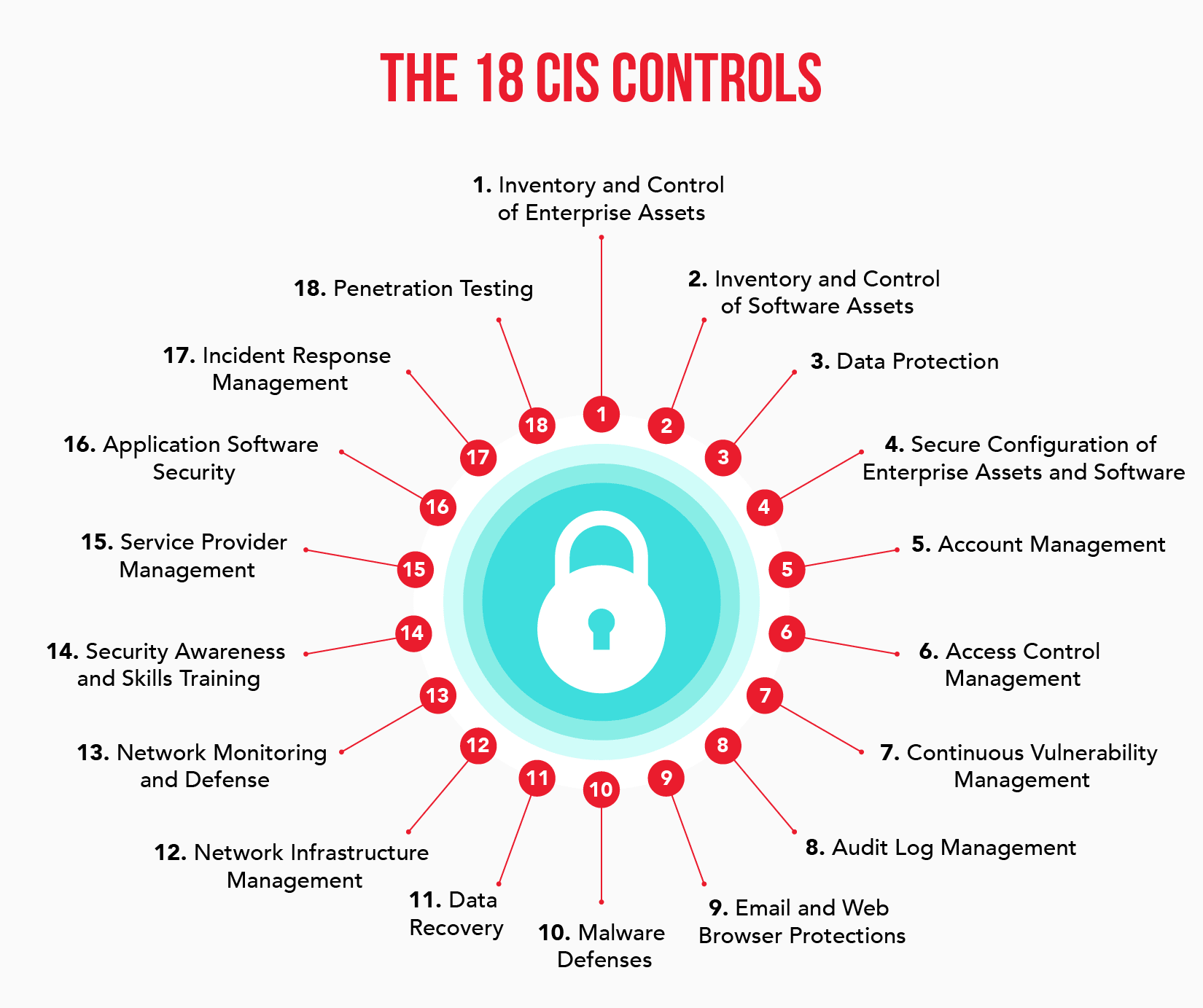
The most recent version (version 8) of the CIS framework consists of 18 Critical Security Controls organized by activity and function. These controls are based on real-world incidents, expert consensus, and industry best practices, making them highly relevant and effective for organizations of all sizes and industries.
By implementing these 18 Controls, organizations can create a more comprehensive cybersecurity strategy that enhances their overall resilience to cyber threats.
What Are the 18 Critical Security Controls?
The 18 Critical Security Controls published by the Center for Internet Security act as a cybersecurity framework for organizations of all shapes and sizes, providing leaders and decision-makers with a clear set of protocols and policies that are considered consensus best practices by cybersecurity experts and educators alike.
These controls address important aspects of a comprehensive cybersecurity strategy like data protection, user authorization, and penetration testing.
The following sections take a closer look at all 18 of the current Critical Security Controls by the CIS.
1. Inventory and Control of Enterprise Assets
The first Control deals with tracking and managing hardware inventory. This includes end-user devices, network devices, any tech that belongs to the Internet of Things (IoT), servers, and anything else that is connected to the IT infrastructure.
Tracking this inventory helps to identify unknown/unauthorized assets that staff is using regularly. From there, you can properly support, restrict, or eliminate assets as necessary.
Inventory management gives you a better view of the whole picture when it comes to network enabled devices.
2. Inventory and Control of Software Assets
In the same vein as hardware inventory management, the second Control takes care of tracking and managing software-based assets. You want to have full transparency over the programs and operating systems being used across the network and this Control provides just that.
With this software map in hand, you can ensure that only authorized software is being used and eliminate or block any unauthorized programs.
3. Data Protection
Data protection combines the efforts of data privacy and data security tactics to truly fortify any data living on the network. These efforts are also sometimes referred to collectively as information security.
More specifically, data protection involves a series of security tactics that an organization employs to maintain data confidentiality, integrity, and availability. This typically includes user verification and authentication, detection and response plans, and an emergency backup and disaster recovery strategy.
Emphasizing the importance of data privacy and data security in your network defenses will help you securely handle, store, and use data ultimately keeping you, your staff, and your clients safe at all times.
4. Secure Configuration of Enterprise Assets and Software
After identifying hardware and software assets, proper configurations must be established to maintain network security and supplement authorization protocols.
Simply said, you don't want to put your security standards in the hands of default settings. Rather, your IT and cybersecurity teams should work hand-in-hand to customize device and software settings to the unique network environment.
Proper security configuration will also require the identification of open ports across your network. Open ports are essentially virtual connection points that facilitate the transfer of information and data.
As such, any open ports discovered need to be assigned a set of strict rules that deny any unknown or unauthorized connections.
Even simple Secure Sockets Layer (SSL) certifications that encrypt communications between users and websites are a crucial aspect of secure configuration.
5. Account Management
Account management is the first Control that’s almost entirely rooted in the principles of identity and access management, which works to authenticate and verify users as they access data across the network. One pillar in account management is security clearance assignment.
To mitigate unauthorized access to data, accounts, and the network, organizations can create user accounts with a certain level of security clearance. In other words, one user’s compromised credentials would only take a threat actor so far, greatly reducing the amount of damage an unauthorized user could inflict.
A standard operating rule to keep in mind when thinking about account management is that employees should only have access to data if absolutely necessary.
6. Access Control Management
Another major aspect of identity access management involves access control in addition to account management. Where account management focuses on assigning the appropriate level of security clearance to accounts across the network, access management creates protocols around user authorization and verification.
Multi-factor authentication (MFA) is one of the best ways that organizations can maintain regular user authentication and verification. In addition, zero trust security frameworks that operate with a “never trust, always verify” model are gaining traction as a cybersecurity solution for the modern work environment.
7. Continuous Vulnerability Management
The cybersecurity space is advancing at an almost unbelievable rate and it’s up to you to keep pace.
This is why conducting regular vulnerability and cyber risk audits that allow you to identify new gaps in your security, track and isolate threats, and implement software patches as necessary is so crucial.
Having these audits done by a third party is integral to avoid bias and to garner the most complete picture of your organization’s cyber risk level.
8. Audit Log Management
Audit logs are essentially massive event records, keeping track of the activities on network devices, software platforms, and other pieces of the IT infrastructure. Analyzing these logs provides valuable insights to cybersecurity professionals in identifying and investigating security incidents, and in ensuring regulatory compliance as well.
Audit log management helps to continually improve your cybersecurity strategy as it can reveal deep insights into network activity and help you uncover valuable patterns that can inform additional actions.
9. Email and Web Browser Protections
Your employees are both your biggest asset and largest cybersecurity vulnerability. With tools that help identify and neutralize threats that come through emails or web browsers, though, you’ll give your employees a better chance at avoiding security incidents altogether.
Email and web browser protections include things like:
- Spam filtering
- Phishing detection and reporting
- Attachment scanning
- Safe browsing warnings
- Malicious website blocking
- Custom privacy controls
Though they aren’t a guarantee, these tools greatly improve your cybersecurity posture as a whole by improving environmental defense. It's also important to note that these tools will be largely influenced by the continual advancement, development, and integration of AI.
10. Malware Defenses
Malware defense as a Critical Security Control assists organizations in preventing malware from infiltrating the network.
Some of the most common examples of malware defense include modern antivirus, firewalls, and malware scanners. Antivirus and malware scanners work in concert to regularly look for and identify computer viruses or hidden malware lurking in the back of your network, while firewalls gatekeep digital communications between users and websites.
These are critical security tools in guarding your network against external threats and malware attacks.
11. Data Recovery
A massive arm of cybersecurity focuses solely on backup disaster and recovery. One of the core functions of backup and disaster recovery is all about prompt data recovery that gets your business up and running again in the wake of a cybersecurity or data loss incident.
With a proper data recovery plan established, you significantly reduce how long it will take your organization to recover operations following a cyberattack, and in turn, how much total damage is done.
12. Network Infrastructure Management
Network infrastructure management is the Critical Security Control that focuses on an organization’s data flow. Network infrastructure management is kind of like designing a highway that gets people where they need to go in an orderly fashion, all while avoiding bottlenecks and major accidents.
On the highway, this is about efficiency and safety, but in network infrastructure, managing data flows helps avoid network crashes caused by too much traffic, eliminates data loss, and ensures consistent data availability.
13. Network Monitoring and Defense
By monitoring your attack surface, you can better predict and prepare for incoming threats. In the context of cybersecurity, network monitoring allows you to identify potential threats by unusual or suspicious user and device behavior, data patterns, or event anomalies.
With a proper network monitoring strategy in place, you’ll be able to detect, predict, and neutralize malicious activity with more accuracy and speed.
14. Security Awareness and Skills Training
Employee cybersecurity awareness training is essential in preventing cyberattacks that manipulate individuals into giving away sensitive information like user credentials.
By educating your staff on phishing scams, and other common social engineering schemes, you’ll greatly reduce the risk of a user-based cybersecurity incident.
Organizations should conduct an introductory cybersecurity awareness training as a standard part of their onboarding process and should supplement this initial training with regularly scheduled refresher training.
15. Service Provider Management
If you’re going to work with a managed security service provider (MSSP) to handle any or all of your cybersecurity needs, you’ll need to implement an evaluation and audit process. These evaluations help you get the most value out of the partnership while ensuring that your data is secure and that your organization is adhering to applicable compliance regulations.
By conducting thorough evaluations, you’ll be able to partner with the security provider that makes the most sense for your organization.
16. Application Software Security
Cybersecurity teams have so much going on that sometimes application software security simply gets overlooked. Think about the last time you or someone on your staff took the time to install a security patch for your office’s smart thermostat.
Although it’s easy to slip up here, keeping any software in use throughout the organization updated with security protocols will help you address any security vulnerabilities that come about before they can be exploited.
17. Incident Response and Management
If a significant cybersecurity incident should occur on your network, it’s imperative that your organization has an action plan in place that can be executed immediately. Incident response and disaster recovery plans form the backbone of a powerful cybersecurity strategy that will get your business back up and running even in a worst case scenario.
18. Penetration Testing
Penetration testing is a service offered by white-hat hackers who use hacking to help businesses improve their cybersecurity strategies. It involves programmers launching simulated cyberattacks against an established business to discover vulnerabilities and defense tactics for the newest and most sophisticated cyberattacks available. These simulated attacks make use of real cyberattack tactics and are effective in revealing existing network vulnerabilities.
White hat hackers aim to improve cybersecurity in an organization, operating in contrast to black hat hackers who are most often after personal or financial gain.
Penetration testing is an excellent way for organizations to test their cybersecurity strategy against real-world threats while uncovering opportunities for continual improvement.
Final Thoughts on the Version 8 CIS Critical Security Controls
Taking on a 50,000-piece jigsaw puzzle by yourself might be a little bit dizzying, and this is only made worse if you aren’t an avid puzzler to begin with. Developing a cybersecurity strategy from scratch can feel just as overwhelming without any guidance.
Organizations can use the 18 Critical Security Controls published by the Center for Internet Security to identify, plan, and implement cybersecurity protocols and policies considered best practices across the industry.
Start your journey toward a more secure tomorrow with help from the Critical Security Controls listed in version 8 and a team of external experts ready to help with implementation and execution.